by Ashley Burrus | May 1, 2024 | Uncategorized
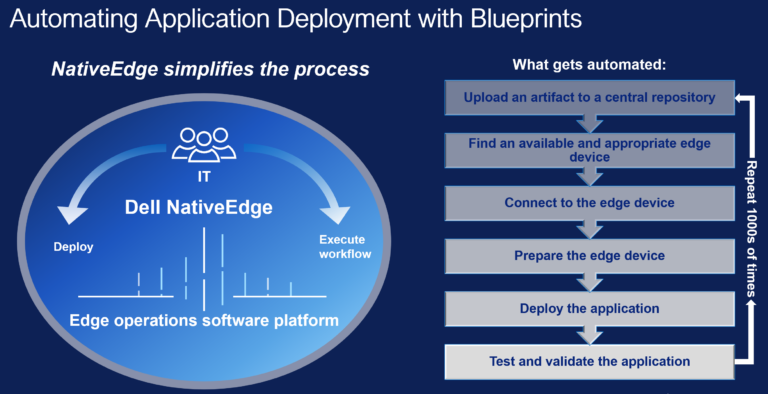
In today’s fast-paced digital world, businesses seek ways to stay ahead, accelerate operations, and leverage new technologies. One technology revolutionizing business operations is edge computing. At the forefront of this transformation is Dell NativeEdge 2.0 –...

by Ashley Burrus | Apr 10, 2024 | Uncategorized
Cure What Ales You In today’s rapidly evolving cybersecurity landscape, ensuring robust protection is no longer optional but imperative. How would your company respond to an unforeseen ransom demand? Astonishingly, only 23% of organizations possess a prepared...

by Ashley Burrus | Mar 5, 2024 | Uncategorized
In today’s digital age, strong cybersecurity is crucial. Bitdefender stands at the forefront of this battle. Founded in 2001, Bitdefender has become a global leader in antivirus and internet security solutions. Bitdefender’s dedication to excellence is evident in its...

by Ashley Burrus | Feb 19, 2024 | Uncategorized
In every company, the unique stories of its team members often reveal deep connections and personal journeys. As we wrap up our series on influential figures at vTECH io, we turn our focus to DJ Peterson. His story is a blend of family legacy and new ideas, showcasing...

by Ashley Burrus | Feb 13, 2024 | Uncategorized
Anyone who has worked with vTECH io in the last 12 years has interacted with Rob Krug, our next vTECH io key employee. Whether it’s face-to-face or behind the scenes, Rob is involved in every aspect of vTECH io’s cybersecurity. He is a seasoned expert with...

by Ashley Burrus | Feb 5, 2024 | Uncategorized
There has been a major shift in the powerhouses of IT companies. On November 22nd 2023, Broadcom acquired VMWare for $61 Billion in cash and stock. This is one of the biggest takeover deals in the technology sector. The acquisition of VMware by Broadcom represents a...







